In An Infrastructure Basic Service Set (Bss), How Does The Passive Scanning Process Occur?
Before using any network, you must get-go find it. With wired networks, finding the network is easy: expect for the cablevision or a jack on the wall. In the wireless earth, stations must identify a compatible network before joining it. The process of identifying existing networks in the area is called scanning.
Several parameters are used in the scanning procedure. These parameters may exist specified by the user; many implementations take default values for these parameters in the driver.
BSSType (independent, infrastructure, or both)
Scanning can specify whether to seek out independent ad hoc networks, infrastructure networks, or all networks.
BSSID (individual or broadcast)
The device can scan for a specific network to join (private) or for whatsoever network that is willing to allow it to join (broadcast). When 802.11 devices are moving, setting the BSSID to circulate is a skillful idea because the browse results will include all BSSs in the area.
SSID ("network name")
The SSID assigns a cord of bits to an extended service gear up. Almost products refer to the SSID every bit the network proper name because the cord of $.25 is commonly set to a human-readable string. Clients wishing to detect whatsoever network should set this to the broadcast SSID.
ScanType (active or passive)
Active scanning uses the transmission of Probe Asking frames to identify networks in the area. Passive scanning saves bombardment power past listening for Beacon frames.
ChannelList
Scans must either transmit a Probe Request or heed on a channel for the existence of a network. 802.11 allows stations to specify a listing of channels to effort. Products let configuration of the channel list in different ways. What exactly constitutes a channel depends on the physical layer in use. With directly-sequence products, it is a list of channels. With frequency-hopping products, information technology is a hop design.
ProbeDelay
This is the delay, in microseconds, before the process to probe a channel in agile scanning begins. This filibuster ensures that an empty or lightly loaded channel does non completely cake the scan.
MinChannelTime and MaxChannelTime
These values, specified in time units (TUs), specify the minimum and maximum amount of time that the scan works with any item aqueduct.
Passive Scanning
Passive scanning saves battery power because it does not require transmitting. In passive scanning, a station moves to each aqueduct on the channel listing and waits for Beacon frames. Any Beacons received are buffered to extract data about the BSS that sent them.
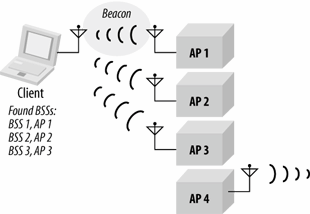
In the passive scanning process, the station sweeps from channel to channel and records information from any Beacons information technology receives. Beacons are designed to allow a station to find out everything information technology needs to match parameters with the bones service set (BSS) and begin communications. In Figure 8-2, the mobile station uses a passive scan to find BSSs in its area; it hears Beacon frames from the outset iii access points. If it does non hear Beacons from the quaternary access bespeak, it reports that only iii BSSs were found.
Figure 8-2. Passive scanning
Active Scanning
In agile scanning, a station takes a more assertive role. On each channel, Probe Request frames are used to solicit responses from a network with a given proper name. Rather than listening for that network to announce itself, an agile scan attempts to find the network. Stations using active scanning utilize the following procedure for each channel in the channel listing:
- Move to the aqueduct and wait for either an indication of an incoming frame or for the ProbeDelay timer to expire. If an incoming frame is detected, the channel is in use and can be probed. The timer prevents an empty channel from blocking the entire procedure; the station won't wait indefinitely for incoming frames.
- Proceeds access to the medium using the bones DCF access procedure and send a Probe Asking frame.
- Wait for the minimum channel time, MinChannelTime, to elapse.
- If the medium was never busy, there is no network. Movement to the next channel.
- If the medium was decorated during the MinChannelTime interval, await until the maximum time, MaxChannelTime, and process any Probe Response frames.
Probe Response frames are generated by networks when they hear a Probe Asking that is searching for the extended service prepare to which the network belongs. At a party, you might wait for a friend by wandering effectually the trip the light fantastic floor shouting out her name. (It'southward not polite, but if you actually want to discover your friend, you may not accept much option.) If your friend hears you, she will respondothers volition (y'all promise) ignore you. Probe Request frames function similarly, simply they can also employ a broadcast SSID, which triggers a Probe Response from all 802.11 networks in the area. (Information technology'due south like shouting "Fire!" at the partythat's sure to outcome in a response from everybody!)
One station in each BSS is responsible for responding to Probe Requests. The station that transmitted the last Beacon frame is also responsible for transmitting whatever necessary Probe Response frames. In infrastructure networks, the access points transmit Beacons and thus are likewise responsible for responding to itinerant stations searching the area with Probe Requests. IBSSs may pass effectually the responsibility of sending Beacon frames, so the station that transmits Probe Response frames may vary. Probe Responses are unicast direction frames and are therefore subject to the positive acknowledgment requirement of the MAC.
Information technology is common for multiple Probe Responses to be transmitted as a event of a single Probe Asking. The purpose of the scanning procedure is to observe every basic service area that the scanning station can join, then a broadcast Probe Request results in a response from every access point within range. Any overlapping independent BSSs may too respond.
Figure 8-3 shows the human relationship between the transmission of Probe frames and the diverse timing intervals that can be configured equally part of a scan.
Figure eight-iii. Agile scanning procedure and medium admission
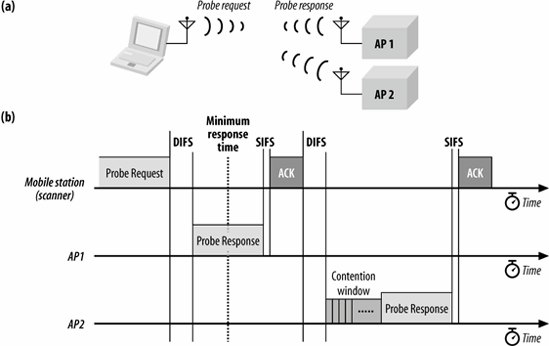
In Figure 8-3 (a), a mobile station transmits a probe request to which two access points respond. The activity on the medium is shown in Effigy eight-3 (b). The scanning station transmits the Probe Request after gaining access to the medium. Both access points answer with a Probe Response that reports their network's parameters. Note that the 2d Probe Response is bailiwick to the rules of the distributed coordination function and must look for the contention window to expire before transmitting. The get-go response is transmitted before the minimum response time elapses, so the station waits until the maximum response fourth dimension has elapsed before collating the results. In areas with a large number of networks, it may be necessary to adjust the maximum channel time then the responses from all the access points in the area tin can be candy.
Scan Report
A scan study is generated at the conclusion of a browse. The report lists all the BSSs that the scan discovered and their parameters. The complete parameter list enables the scanning station to join whatsoever of the networks that information technology discovered. In addition to the BSSID, SSID, and BSSType, the parameters as well include:[*]
[*] The items actually exposed by any detail software vary.
Buoy interval (integer)
Each BSS tin can transmit Beacon frames at its own specific interval, measured in TUs.
DTIM menstruum (integer)
DTIM frames are used every bit part of the powersaving machinery.
Timing parameters
Ii fields aid in synchronizing the station'due south timer to the timer used past a BSS. The Timestamp field indicates the value of the timer received by the scanning station; the other field is an offset to enable a station to lucifer timing information to join a item BSS.
PHY parameters, CF parameters, and IBSS parameters
These three facets of the network have their own parameter sets, each of which was discussed in detail in Chapter four. Channel information is included in the physical-layer parameters.
BSSBasicRateSet
The basic rate set is the list of data rates that must be supported by any station wishing to bring together the network. Stations must exist able to receive data at all the rates listed in the set. The basic rate set is equanimous of the mandatory rates in the Supported Rates information element of management frames, as in Chapter four.
What s in a Proper noun? (or, the Security Fallacy of Hidden SSIDs)
WEP is not required by 802.11, and a number of earlier products implement only open up-system authentication. To provide more security than straight open-arrangement authentication allows, many products offering an "authorized MAC address list." Network administrators can enter a listing of authorized client addresses, and only clients with those addresses are allowed to connect.
The SSID is an important scanning parameter. Stations search for an SSID when scanning, and may build a list of SSIDs for presentation to the user. Every bit a unique identifier for a network, the SSID is often given mythic security backdrop information technology does not actually possess.
At the dawn of 802.11, the SSID was broadcast in the clear in Beacon frames, correct in that location for the listening. All that was necessary was an 802.xi interface tuned to the correct radio channel. When the stone age of 802.11 began, 1 vendor began to treat the SSID as a valuable security token. Past enabling the "closed network" option on that vendor's equipment, the SSID was no longer put in Buoy frames, thus "protecting" the network from attackers. To further "protect" the SSID from prying optics, access points operating a closed network would non reply to Probe Requests with the broadcast SSID.
Closed networks break passive scanning because the SSID is no longer available for easy collection. In gild to prevent a closed network from being completely closed to clients, however, access points must respond to Probe Requests containing the correct SSID. Management frames have no encryption, and the SSID value is right there for the taking in the Probe Asking. To be scrupulously right, the closed network may offer a vanishingly small incremental amount of security because the SSID is only bachelor when stations search for the network, rather than several times per 2d in Beacon frames.
Hiding an SSID tin can cause issues with 802.11 management. Although most 802.xi interfaces and their associated drivers can handle subconscious SSIDs, not all can. Hiding an SSID is a nonstandard procedure that can cause problems, and does not provide any real security. Leave the SSID in the Buoy frames for interoperability, and employ a real security solution like 802.1X if yous demand information technology.
Joining
After compiling the scan results, a station can elect to bring together ane of the BSSs. Joining is a precursor to association; it is analogous to aiming a weapon. It does not enable network admission. Before this can happen, both authentication and clan are required.
Choosing which BSS to join is an implementation-specific decision and may even involve user intervention. BSSs that are part of the aforementioned ESS are allowed to make the conclusion in any fashion they choose; common criteria used in the decision are ability level and signal strength. Observers cannot tell when a station has joined a network considering the joining process is internal to a node; information technology involves matching local parameters to the parameters required past the selected BSS. One of the about important tasks is to synchronize timing data betwixt the mobile station and the rest of the network, a process discussed in much more detail in the section "Timer Synchronization," later in this chapter.
The station must also lucifer the PHY parameters, which guarantees that any transmissions with the BSS are on the right channel. (Timer synchronization also guarantees that frequency-hopping stations hop at the right time, as well.) Using the BSSID ensures that transmissions are directed to the correct set of stations and ignored by stations in some other BSS.[*] Adequacy data is besides taken from the scan result, which matches the use of WEP and whatever high-rate capabilities. Stations must too adopt the Buoy interval and DTIM period of the BSS, though these parameters are not every bit important every bit the others for enabling communication.
[*] Technically, this is true only for stations obeying the filtering rules for received frames. Malicious attackers intent on compromising network security can easily choose to disobey these rules and capture frames, and most existing product implementations do not correctly implement the filtering rules.
In An Infrastructure Basic Service Set (Bss), How Does The Passive Scanning Process Occur?,
Source: https://flylib.com/books/en/2.519.1/scanning.html#:~:text=In%20passive%20scanning%2C%20a%20station,from%20any%20Beacons%20it%20receives.
Posted by: bratcherwithile1984.blogspot.com


0 Response to "In An Infrastructure Basic Service Set (Bss), How Does The Passive Scanning Process Occur?"
Post a Comment